|
 |
 |
 |
 |
  |
|||
 |
 |
 |
|
|
Acunetix Web Vulnerability Scanner is a highly customisable, regularly updated and fully supported web application scanner which allows the tester to thoroughly check for a plethora of current web application vulnerabilities.
Acunetix uses bespoke AcuSensor Technology allowing the identification of more vulnerabilities than with other current web application scanners with extremely low false positives being recorded. This technology also provides details of specific vulnerabilities identified within the web apps code and reports debug information.
AcuSensor Technology - Insight/ Evaluation
AcuSensor Technology talks to the web server and determines the sites configuration and coding language (PHP and .NET et al), it also allows a return of a full directory listing, including files not viewable via normal web links :-) A list of all available application inputs is also enumerated, once all this is known a broader range of tests is performed against the application.
One nice little piece of technology integrated in AcuSensor is the way it hooks in between the web application itself and the backend database, allowing the ability to trace SQL injection vulnerabilities in the code against relying on database errors to determine vulnerabilities. For reporting details such as source code line number, stack trace, affected SQL query etc. are a major plus for code developers to perform quick remedial action on the affected application.
There's detailed information about this new technology available from here.
This new technology recently found an 0day, more details can be found here.
Vulnerability Checks
Currently Acunetix carries out multiple pre-defined checks for the following vulnerabilities:
Specific profiles are installed by default to aid the tester, however, bespoke profiles are easily creatable and can be up and running within seconds.
Port Scanner/ Service and Vulnerability Enumeration
Another tool added to Acunetix which will provide huge benefits to Acunetix users is the ability to perform Port Scanning and enumerate and assess the discovered open services for well-known vulnerabilities'. We may now see the first steps away from just being a dedicated Web Application Scanner to an all purpose excellent Web and fully-armed Network scanner. The fact that these service detection and vulnerability checks can be scripted and new ones custom written is an excellent feature and akin to the nasl scripts available and customisable in Nessus. I expect this feature will grow and grow.
Currently Acunetix allows you to conduct:
Other benefits now offered with version 6 is the ability to:
Acunetix also provides a number of test sites to test their demonstration version of the application against deploying all major web app technologies:
http://testasp.acunetix.com
In addition to its automated scanning engine, Acunetix includes advanced tools including the ability to perform SQL Blind Injection to allow penetration testers to fine tune web application security checks allowing the tester to use:
Acunetix is also able to automatically fill in web forms and authenticate against web logins. Most web vulnerability scanners are unable to do this or require complex scripting to test these pages.
Acunetix trial full: http://www.acunetix.com/vulnerability-scanner/download.htm
Acunetix free: http://www.acunetix.com/cross-site-scripting/scanner.htm
Installation:
Simply download and install (and register) Select to install Firefox Plugin - A review of this can be found here.
Execution:
Two Modes:
Wizard process Selecting New Scan. Input URL/ IP or Browse to new or save target file. Acunetix will automatically detect (or the user can specify) the targets server-side web technologies deployed to fully tailor and optimise the scan. Crawling Options - Specify verbosity level for site crawling. Scan Options - Select pre-defined (or user created) profile and scannig mode i.e. Quick, Extensive, Heuristic etc. Authentication Details - User supplied credentials or Recorded Login Sequence. Finish (i.e. Execute)
Manual Select specific Tool Input required information i.e. URL, Authentication Method/ Error Codes etc. Select Start
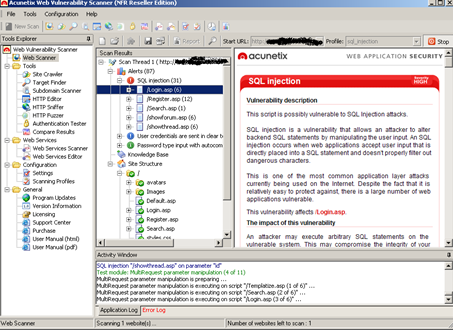
An explorer type window details the Site Structure and any alerts found with full descriptions of any vulnerabilities' identified. Included within this are links to Acunetix knowledgebase articles and helpful www links to resources.
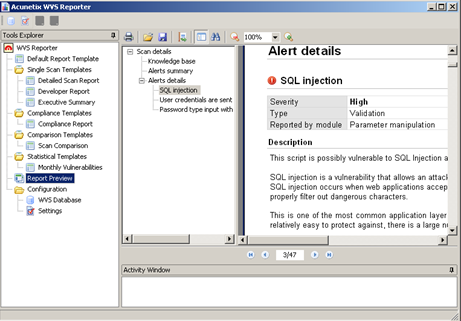
Acunetix includes an extensive reporting module which can generate reports that can be tailored dependant on your clients requirements. The Compliance Report template is especially useful allowing you to demonstrate compliance against the requirements of HIPAA, NIST, PCI, Sarbanes Oxley and recommendations made by the Web Application Security Consortium: Threat Classification.
Reporting can be produced in a plethora of formats including pdf, html, text, word and bmp
Version 5 Vs Version 6
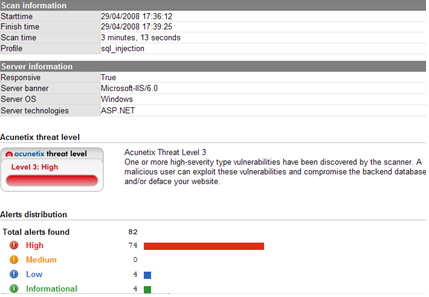
A test was carried out against http://testphp.acunetix.com using the blind sql injection pre-configured profile with both versions of the scanner with all associated patches and updates applied. A large difference in reported results was obtained:
The medium vulnerabilities identified were missed by version 5 and could should they have been exploited have amounted to possible remote code execution and information disclosure on the remote vulnerable server!
You will notice there is a lot more informational alerts being found, these although not necessarily expressing any details of vulnerabilities in the system are highly valuable for customer feedback, detailing files found in publically available directories that are not linked directly from the site, these of course could contain sensitive configuration information, scripts, credentials and the like so should not be overlooked and investigated thoroughly.
Version 6 seemed to carry out a better job of spidering/crawling the remote web application, returning 7 extra web directories on the server, possible extra cookie values etc.
Version 5 was slightly quicker in the test taking 2 mins 33 secs, version 6 took 2 mins 59 seconds.
In essence, version 6 is a big step ahead with increased functionality, reporting and identification of potential problems and vulnerabilities.
Definitely worth the upgrade if using version 5!
Summary:
An excellent tool and my Web Application Scanner of choice. Thoroughly extensible and with some excellent bespoke features missing from similar products. Definitely add this to your toolset!
|
IT Security News:
Pen Testing Framework:
Latest Tool Reviews:
Information:
|
| © VulnerabilityAssessment.co.uk 16 April 2009 |
|