|
Web Application Attack and Audit Framework (W3AF)
w3af is a Web Application Attack and Audit Framework. The project goal is to create a framework to find and exploit web application vulnerabilities that is easy to use and extend.
The project uses a number of disparate plugins to carry out an audit against a target website, the main ones being:
Discovery plugins have only one responsibility, finding new URLs, forms, and other “injection points”. A classic example of a discovery plugin is a web spider. This plugin takes a URL as input and returns one or more injection points. When a user enables more than one plugin of this type, they work recursively: If plugin A finds a new URL in the first run, the w3af core will send that URL to plugin B. If plugin B then finds a new URL, it will be sent to plugin A. This will go on until all plugins are run and no more knowledge about the application can be found using the enabled discovery plugins. Audit plugins take the injection points found by discovery plugins and send specially crafted data to all of them in order to find vulnerabilities. A classic example of an audit plugin is one that searches for SQL injection. Attack plugins objective is to exploit vulnerabilities found by audit plugins. They usually return a shell on the remote server, or a dump of remote databases in case of SQL injections.
The plugins find the URLs, discover the bugs and exploit them. The complete list of plugins types is:
audit bruteforce discovery evasion exploit grep mangle output
It is available from here.
Installation:
Pre-requisites:
Unbundled:
pyOpenSSL - yum install pyOpenSSL
Bundled with w3af:
cd w3af/extlib
cd fpconst-0.7.2
python setup.py install
cd pygoogle
python setup.py install
cd pywordnet
python setup.py install
cd SOAPpy
python setup.py install
cd pyPdf
python setup.py install
Execution: Either command-line of gtk GUI are available
./w3af [options]
Options:
-h Print this help message.
-s <file> Execute a script file.
-g Run GTK user interface.
-i <dir> Directory where MSF is installed (only used to install the virtual daemon).
-p <profile> Run with the selected profile
./w3af -g brings up the GUI, right click empty profile and select and appropriate name for the new profile. Select the requisite plugins you want to test against the site Insert the url of the target. 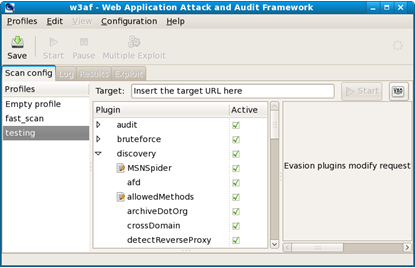
After pressing start you are taken to the log tab which records all associated output generated by the tool and hopefully any vulnerabilities found:
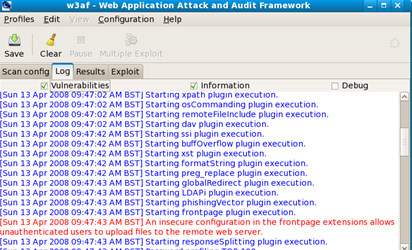
Selecting the results tab will provide more details of problems within the site: 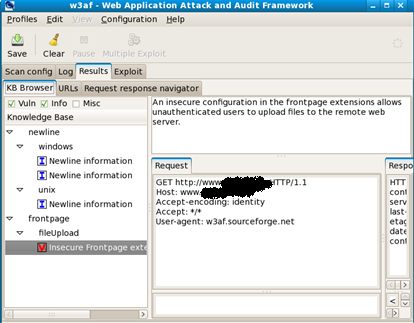
The final tab exploit will actually allow you to launch any found exploits :-)
This is a really nice tool and getting better with every release, one to have!
| 













