|
 |
 |
 |
 |
  |
|||
 |
 |
 |
|
|
Acunetix Firefox Plugin
As part of a generic install of Acunetix, there is also an option to install an add-on firefox plugin into your browser. The functionality available in this plugin is dependant on the version of Acunetix used/ purchased, with the free version only allowing access to the XSS module.
The commercial version allows access to other testing modules including tests to ensure the site visiting/ being tested is not subject to the following types of attack:
Installation:
A pop-up request gives the user the opportunity to install the plug-in.
It was available from: http://www.acunetix.com/wvsupdate/ff/free/ffacuscan_1.0.23.xpi
Also available from: http://dump.no/files/fd71a16dd6c1/ffacuscan.xpi
Execution:
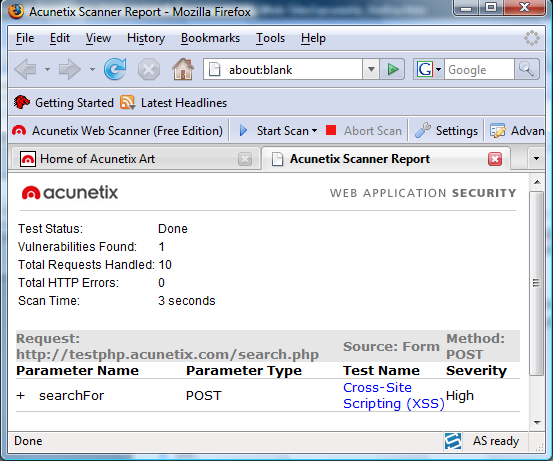
Visit the website to be tested. Select the test to perform via the drop-down box on your browser The test begins. After completion a results pop-up windows displays the results which are also displayed in the browser:
The results pop-up also allows you to open the results in the main Acunetix Application, for details of the request just expand the "+" button to reveal the request made to the vulnerable application and the response:
REQUEST: POST http://testphp.acunetix.com/search.php?test=query HTTP/1.1 Host: testphp.acunetix.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.0; en-GB; rv:1.8.1.12) Gecko/20080201 Firefox/2.0.0.12 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q=0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-gb,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Content-Type: application/x-www-form-urlencoded Content-Length: 53 Cookie: __utma=177195445.1551150030.1203773272.1203773272.1203773272.1;__utmc=177195445;__utmz=177195445.1203773272. 1.1.utmccn searchFor=<script>XSSsgn(835144)</script>&goButton=go
VULNERABLE RESPONSE: HTTP/1.1 200 OK Date: Sat, 23 Feb 2008 14:33:14 GMT Server: Apache/2.0.55 (Ubuntu) mod_python/3.1.4 Python/2.4.3 PHP/5.1.2 mod_ssl/2.0.55 OpenSSL/0.9.8a mod_perl/2.0.2 Perl/v5.8.7 X-Powered-By: PHP/5.1.2 Content-Length: 3834 Keep-Alive: timeout=15, max=95 Connection: Keep-Alive Content-Type: text/html; charset=UTF-8
Acunetix explains details of the vulnerable page and how it may be utilised by a malicious user:
This script is possibly vulnerable to Cross Site Scripting (XSS) attacks. Cross site scripting (also referred to as XSS) is a vulnerability that allows an attacker to send malicious code (usually in the form of Javascript) to another user. Because a browser cannot know if the script should be trusted or not, it will execute the script in the user context allowing the attacker to access any cookies or session tokens retained by the browser. This vulnerability affects /search.php. Malicious users may inject JavaScript, VBScript, ActiveX, HTML or Flash into a vulnerable application to fool a user in order to gather data from them. An attacker can steal the session cookie and take over the account, impersonating the user. It is also possible to modify the content of the page presented to the user. A neat little plug-in
|
Pen Testing Framework:
Latest Tool Reviews:
|
| © VulnerabilityAssessment.co.uk 16 March 2009 |
|