|
 |
 |
 |
 |
  |
|||
 |
 |
 |
|
|
Metasploit 3
The Metasploit Framework consists of tools, libraries, modules, and user interfaces. The basic function of the framework is a module launcher, allowing the user to configure an exploit module and launch it at a target system. If the exploit succeeds, the payload is executed on the target and the user is provided with a shell to interact with the payload.
Installation:
Windows - Simply double-click on the executable.
Unix -
Requires ruby to be installed prior to extraction and compilation [root@FC9 ~]# yum install ruby ruby-irb ruby-libs ruby-rdoc ruby-devel readline rubygems Loaded plugins: refresh-packagekit livna | 2.1 kB 00:00 primary.sqlite.bz2 | 4.3 kB 00:00 fedora | 2.4 kB 00:00 updates-newkey | 2.3 kB 00:00 primary.sqlite.bz2 | 3.3 MB 01:01 updates | 2.6 kB 00:00 Setting up Install Process Parsing package install arguments Package readline-5.2-13.fc9.i386 already installed and latest version Resolving Dependencies Dependencies Resolved ================================================================================ Package Arch Version Repository Size ================================================================================ Installing: ruby i386 1.8.6.287-2.fc9 updates-newkey 525 k ruby-devel i386 1.8.6.287-2.fc9 updates-newkey 796 k ruby-irb i386 1.8.6.287-2.fc9 updates-newkey 285 k ruby-libs i386 1.8.6.287-2.fc9 updates-newkey 1.7 M ruby-rdoc i386 1.8.6.287-2.fc9 updates-newkey 353 k rubygems noarch 1.2.0-2.fc9 updates-newkey 599 k Installed: ruby.i386 0:1.8.6.287-2.fc9 ruby-devel.i386 0:1.8.6.287-2.fc9 ruby-irb.i386 0:1.8.6.287-2.fc9 ruby-libs.i386 0:1.8.6.287-2.fc9 ruby-rdoc.i386 0:1.8.6.287-2.fc9 rubygems.noarch 0:1.2.0-2.fc9 Complete! [root@FC9 ~]# gem install -v=1.2.2 rails Successfully installed rake-0.8.3 Successfully installed activesupport-1.4.1 Successfully installed activerecord-1.15.2 Successfully installed actionpack-1.13.2 Successfully installed actionmailer-1.3.2 Successfully installed actionwebservice-1.2.2 Successfully installed rails-1.2.2 7 gems installed Installing RDoc documentation for rake-0.8.3... Installing RDoc documentation for activesupport-1.4.1... Installing RDoc documentation for activerecord-1.15.2... Installing RDoc documentation for actionpack-1.13.2... Installing RDoc documentation for actionmailer-1.3.2... Installing RDoc documentation for actionwebservice-1.2.2...For online updates, subversion also requires to be installed Then simply use tar -zxvf framework_version.tar.gz
Updates can be run and use subversion, the command svn update should be run from the framework directory.
It is available from here.
Execution:
Metasploit in Linux can be started a number of ways via the command-line;
./msfweb will load the web version
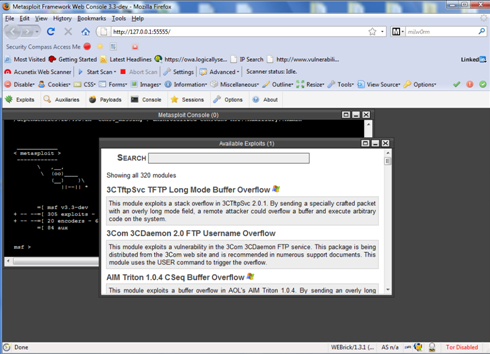
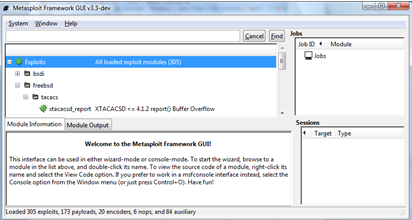
The screen above shows the console and exploits gui already opened.
./msfgui will load the gui
./msfconsole will load the console version.
The following is a simple exploitation of a Windows NT 4 server via the console:
>> use windows/dcerpc/ms03_026_dcom
|
IT Security News:
Pen Testing Framework:
Latest Tool Reviews:
Information:
|
| © VulnerabilityAssessment.co.uk 08 December 2008 |
|