|
 |
 |
 |
 |
  |
|||
 |
 |
 |
|
|
Warify
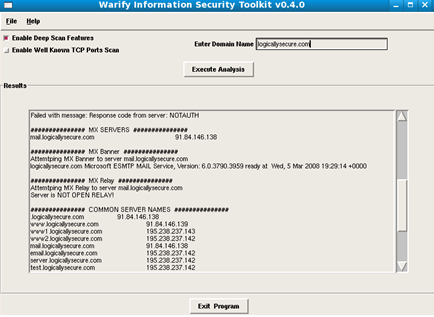
Warify is a platform independent DNS enumeration tool that has the following features:
Optional Features include:
Requirements:
The following perl modules are required:
perl -MCPAN -e 'CPAN::Shell->install( "Tk" )' It is available from here
The author, Bozidar has also a Security Blog you may be interested in which can be found here, some nice Information Security articles and tutorials,worth having a look at.
Execution:
Linux: perl warify.pl
Windows warify.exe
Evaluation:
There are a number of good features for this tool but also correspondingly a number of features that could potentially get a tester into a lot of trouble. The TCP scan feature is not fine-grained enough to limit the scan to the pre-determined main domain and it will merrily scan all enumerated servers, this is especially a problem if those servers do not belong to the enterprise you are testing.
The configuration file warify.conf needs to be tweaked to just scan the most common ports, some innocuous ports are currently listed, in addition the pre-pending defaults should be expanded to include a lot more common server names.
In essence a tool to be aware of, but some work still required.
The current to do list for this version is:
1. Add whois verification functionality
Once this has been carried out I think the tester will have a really useful tool to play with that could be added to the toolbox.
|
IT Security News:
Pen Testing Framework:
Latest Tool Reviews:
|
| © VulnerabilityAssessment.co.uk 09 March 2008 |
|