|
 |
 |
 |
 |
  |
|||
 |
 |
 |
|
|
SSA - Security System Analyzer
SSA is based on OVAL, (Open Vulnerability and Assessment Language), framework brought to you by the people from Mitre
OVAL is an international, information security/community standard that has been designed to:
OVAL includes a language used to encode system details, and an assortment of content repositories held throughout the community. The language standardises the three main steps of the assessment process:
One of the minor drawbacks of using the Mitre OVAL framework is that it is command-line based, which can prove time consuming when scans and updates to the framework need to be performed. SSA has been designed to add a graphical front-end to this process and also provides a great deal more extensibility when utilising the framework in conjunctions with their tool.
SSA is available from here.
Installation:
Just double-click on the .exe
Carry out an update of the product which will download the following files that are required:
Updating itself is very easy and is from preconfigured locations i.e. OVAL and security-database.com and can be altered/ started by clicking on the settings icon on the main screen:
Execution:
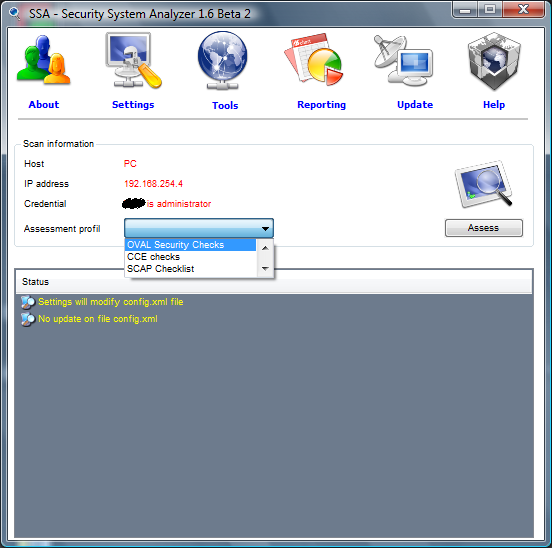
A scan of the local system entails selecting an appropriate Assessment profile, currently available are:
Once the profile has been selected, click on assess:
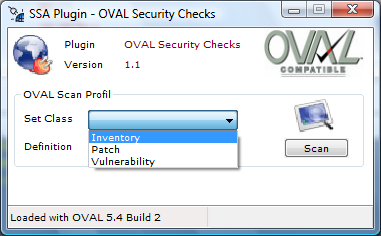
Selecting OVAL security checks then requires you set the class of checks to be carried out i.e. Inventory, Patch or Vulnerability:
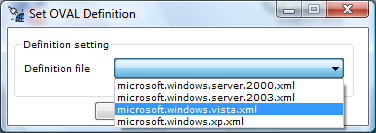
The final stage is to select the platform OS definitions you are scanning against:
Once the scan has been performed, an html page is produced entitled using the format:
date.hostname.profile.class.html i.e. 23-04-2008.PC.oval.Vulnerability.html
Subsequent scans remove this file to an archive location in the logs directory.
Summary:
In essence, I like the product, it is based on a well-supported and regularly updated framework and as such has a solid foundation to forge ahead from. I think there are currently a couple of drawbacks but as of release 1.6 beta 2 it is looking extremely well worth using:
|
IT Security News:
Pen Testing Framework:
Latest Tool Reviews:
|
| © VulnerabilityAssessment.co.uk 23 April 2008 |
|