|
OVAL Interpreter (ovaldi)
OVAL's reference interpreter shows how: information can be collected
from a computer; definitions can be used to test the system for computer
vulnerabilities, configuration issues, programs, and patches; and
results of the tests can be presented.
OVAL is an international, information security/community standard
that has been designed to:
-
Promote open and publicly available security content,
-
Standardise the transfer of this information across the entire spectrum
of security tools and services.
OVAL includes a language used to encode system details, and an
assortment of content repositories held throughout the community. The
language standardises the three main steps of the assessment process:
-
Representing configuration information of systems for testing;
-
Analysing the system for the presence of the specified machine state
(vulnerability, configuration, patch state, etc.);
-
Reporting the results of this assessment.
One of the minor drawbacks of using the Mitre OVAL framework is that it
is command-line based, which can prove time consuming when scans and
updates to the framework need to be performed. SSA has been designed to
add a graphical front-end to this process and also provides a great deal
more extensibility when utilising the framework in conjunctions with
their tool.
It is available from
here.
Installation:
Execution:
Command Line: >ovaldi [option] MD5Hash
Options:
-h
Show options available from command line
-o <string> Path to the definitions xml file DEFAULT="definitions.xml"
-d <string> Save data to the specified XML file DEFAULT="system-characteristics.xml"
-r <string> Save results to the specified XML file DEFAULT="oval-results.xml"
-v <string> Get external variable values from the specified XML file.
DEFAULT="external-variables.xml"
-i <string> Use data from input System Characteristics file
-m
Do not verify the oval.xml file with an MD5 hash
-p
Print all information and error messages
-s
Do not apply a stylesheet to the results xml.
-t <string> Apply the specified xsl to the results xml. DEFAULT="results_to_html.xsl"
-x <string> Output xsl transform results to the specified file.
DEFAULT="results.html"
-z
Return md5 of current definitions.xml
Expected Output:
C:\Program Files\OVAL\ovaldi\ovaldisetup5.1.build14>ovaldi.exe
-o microsoft.windows.xp.definitions.xml -m
----------------------------------------------------
OVAL Definition Interpreter
Version: 5.1 Build: 14
Build date: Nov 3 2006 07:26:32
Copyright (c) 2006 - The MITRE Corporation
----------------------------------------------------
Tue Dec 26 15:32:25 2006
** parsing microsoft.windows.xp.definitions.xml file.
- validating xml schema.
** checking schema version
- Schema version - 5.1
** creating a new OVAL System Charateristics file.
** gathering data for the OVAL definitions.
Collecting object: FINISHED
** saving data model to system-characteristics.xml.
** running the OVAL Definition analysis.
Analyzing definition: oval:org.mitre.oval:def:990
OVAL Id
Result
--------------------------------------------------
oval:org.mitre.oval:def:1002 true
oval:org.mitre.oval:def:105 true
oval:org.mitre.oval:def:521 true
oval:org.mitre.oval:def:425 true
oval:org.mitre.oval:def:666 true
oval:org.mitre.oval:def:415 true
oval:org.mitre.oval:def:310 true
oval:org.mitre.oval:def:475 true
oval:org.mitre.oval:def:764 true
oval:org.mitre.oval:def:100002 true
oval:org.mitre.oval:def:239 true
oval:org.mitre.oval:def:100001 true
oval:org.mitre.oval:def:1557 true
oval:org.mitre.oval:def:1922 true
oval:org.mitre.oval:def:100107 true
oval:org.mitre.oval:def:454 false
oval:org.mitre.oval:def:104 false
------------------abridged---------------
oval:org.mitre.oval:def:844 false
oval:org.mitre.oval:def:886 false
oval:org.mitre.oval:def:889 false
oval:org.mitre.oval:def:898 false
oval:org.mitre.oval:def:900 false
oval:org.mitre.oval:def:921 false
oval:org.mitre.oval:def:925 false
oval:org.mitre.oval:def:926 false
oval:org.mitre.oval:def:958 false
oval:org.mitre.oval:def:962 false
oval:org.mitre.oval:def:963 false
oval:org.mitre.oval:def:964 false
oval:org.mitre.oval:def:968 false
oval:org.mitre.oval:def:974 false
oval:org.mitre.oval:def:983 false
oval:org.mitre.oval:def:989 false
oval:org.mitre.oval:def:990 false
oval:org.mitre.oval:def:419 error
--------------------------------------------------
** finished evaluating OVAL definitions.
** saving OVAL results to results.xml.
** running OVAL Results xsl: results_to_html.xsl.
----------------------------------------------------
The resultant Results.html can then be examined:
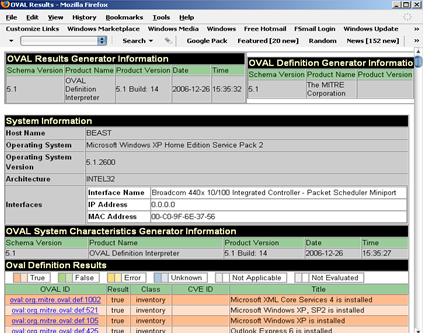
Obviously reviewing the resultant file and playing with the tool itself,
a couple of drawbacks were discovered including:
-
No remote scan option. -
The Results web page unfortunately provides both true and false results
for both the inventory i.e. what's installed and the vulnerabilities
affecting the host. From a vulnerability analysis perspective it
would be more prudent to offer disparate reports i.e. provide a report
that would "grep" for only true results which would indicate a potential
vulnerability on the host. -
The Results page provided potential misleading indicators on the test
machine i.e. reviewing a Windows XP SP2 host with the
microsoft.windows.xp.definitions.xml file provided a result that
Microsoft Windows Server 2003 (Gold) is not installed. This is obviously
true as its an XP host but really superfluous to the test results and
should really be filtered out.
This said, for what you need to know its a pretty solid tool in the
arsenal and the links to potential vulnerability information cannot be
surpassed. Another tool to keep an eye on is the graphical
front-end extension called SSA available from
here. This provides a format that makes scanning an updating
this tool easier alongside the ability to perform remote scans in a
forthcoming release.
| 










