|
 |
 |
 |
 |
  |
|||
 |
 |
 |
|
|
NStalker Enterprise Edition provides a comprehensive and highly customisable Web Security Assessment suite to ensure your application is not susceptible against common vulnerabilities and hacker attacks.
Obviously Web applications go through a distinct stage of development and deployment and as such different facets/ configurations need to be checked and verified prior to release and acceptance by the customer. NStalker have deveoped three bespoke types of scans, (profiles), that can be performed a each stage of the process:
NStalker comprises a number of modules:
Most of NStalker is primarily wizard driven, allowing ease of use and the ability to standardise your assessments. The big advantage, as mentioned before, is the ability to customise your scans dependant on the testing area. In particular, NStalker can also be utilised for compliance testing to ensure for example that inappropriate material has not been made available via your website or forum.
It is available from here
Installation:
Being a windows applications a simple double-click will install the application. A licence has to be procured and installed via the Update Manager. The licensing is particularly useful as you have the ability to attach and detach a licence at anytime allowing transfer between hosts.
Execution: As soon as the application is opened an update will be attempted before the Policy Editor loads. By default the pre-loaded scan wizard offers a choice of the three scan profiles:
Clicking on a choice opens a further windows, where the URL to be tested is supplied and also allows you to change the default test parameters:
The default parameters above will carry out a full test against your application.
Note: - I would suggest, however, a customisation of these as the timescale for completion may be excessive, dependant on the type and size of site due to the extensive Web Spidering Analysis that is carried out.
Once all requirements of the wizard have been completed, the policy editor calls the actual scanner itself with all parameters set that you have just set up The scan will then commence:
To speed up the actual check, if required, you may select the forward arrow buttons, which will skip the current check. Should you need to stop your test before resumption at a later time, this is possible via the Options button. (To restart the test just open the Editor, select the saved session, right click and all stored parameters are loaded and the test resumes.)
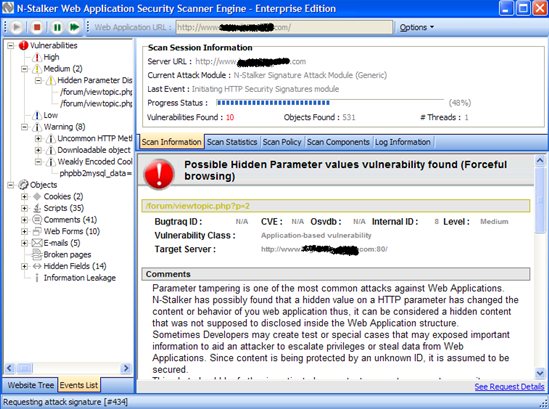
As you can see the scan window has a number of tabs, the Website tree tab displaying the current details of the site being spidered. The Events tab provides the actual vulnerability and information views broken down into severity levels, which will eventually form the reporting sections when the reporting module is called on completion of the test:
I would more rather use the bespoke Policies creation wizard as this provides a more flexible approach to the tester than the default Scan wizard. The is called from the Editor via the Policies and Policy Wizard tab. This takes the form of check parameters that need to be selected to fully customise your test:
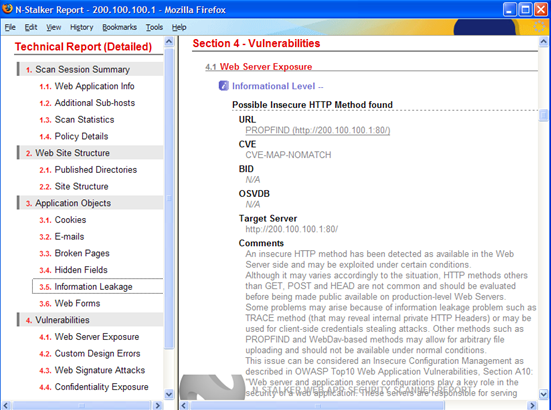
Reporting. There are three types of reports that can be produced, Technical, Comparison and Executive level. Technical Reports: From a technical perspective the most useful sections include:
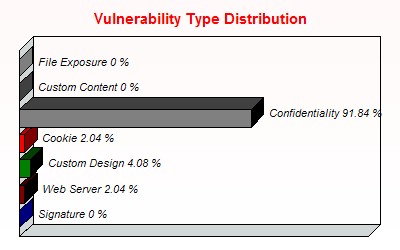
All related findings are included, including suggested fixes and CVE references for further information.
Executive and Comparison Reports: The Executive level report is designed as an overview for managers. The comparison report is both informative and useful as it provides an assessment of changes over a specific period of time of a particular applications and can be used as a guide to ensure that mis-configurations have been fixed (or for that matter re-opened on upgrade.) Personal Assessment:
From a testing perspective, I was a little overawed when I first saw this scanner. It had a number of different parts, wizards, profiles and the like and I thought it would be quite hard to get to know. I was, (happily), proved wrong in this respect and I was very surprised how a decision made in one particular module is carried to another in a logical and common sense approach. The interface is also both intuitive and minimalistic aiding the learning process for a new user.
I would, however, definitely create my own policies rather than use the pre-supplied templates. The web spidering in particular for the site I tested took in excess of 1 hour, (Internet 1/2 Meg link), obviously if you are testing over a LAN this time will be extensively decreased due to higher bandwidth availability, but something to be aware of.
The last check that is performed on a default pen test is an Information Leakage check based on pre-supplied dictionary, this can provide a great deal of false positives and it would be wiser for the tester to use their own particular dictionary, when this check is carried out, (or deselect if not required).
For a quick review, (many web applications can be found running on a single host), quick scans can also be performed utilising 30,000 disparate attack signatures. Again, this can be selected via the Policy wizard which I really like the flexibility of. "Interesting" web applications can then be selected for more thorough testing dependant on the hits returned from the quick scans.
Obviously the depth of scans is dependant on the time you have to conduct an assessment and the amount of applications you need to test and it this balance which must determine your approach to the test.
Overall a solid assessment tool that would definitely find its way into my toolkit.
|
IT Security News:
Pen Testing Framework:
Latest Tool Reviews:
|
| © VulnerabilityAssessment.co.uk 29 February 2008 |
|