|
Microsoft Windows
Nessus Scan
The following is sample output
from a Nessus Scan with all plugins enabled against a Windows XP Home host which
has been fully patched, you can see from the result, theres not a great deal to
go on, besides some brute forcing of named accounts that Nessus has found, maybe
some packet crafting for a DoS and maybe a play with the exported shares:
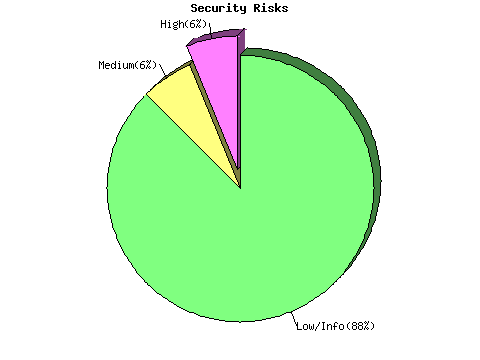
200.100.100.227Repartition of the level of the security problems :
List of open ports :
Information found on port netbios-ssn (139/tcp)
Vulnerability found on port
microsoft-ds (445/tcp)
Sysnopsis :
It is possible to access a network share.
Description :
The remote has one or many Windows shares that can be accessed
through the Network.
Depending on the share rights, it may allow an attacker to
read/write confidential data.
Solution :
To restrict access under Windows, open the explorer, do a right
click on each shares, go to the 'sharing' tab, and click on
'permissions'
Risk factor :
High / CVSS Base Score : 7
(AV:R/AC:L/Au:NR/C:P/A:P/I:P/B:N)
Plugin output :
The following shares can be accessed as nessus9349346341508431342159014881 :
- 70299 - (readable,writable)
+ Content of this share :
CVE : CVE-1999-0519,
CVE-1999-0520
BID : 8026
Nessus ID : 10396
Warning found on port microsoft-ds (445/tcp)
Synopsis :
It is possible to enumerate remote network shares.
Description :
By connecting to the remote host using a NULL (or guest) session
Nessus was able to enumerates the network share names.
Risk factor :
None
Plugin output :
Here is the list of the SMB shares of this host :
IPC$
70299
Nessus ID : 10395
Information found on port microsoft-ds (445/tcp)
Information found on port microsoft-ds (445/tcp)
Synopsis :
It is possible to obtain information about the remote os.
Description :
It is possible to get the remote operating system name and
version (Windows and/or Samba) by sending an authentication
request to port 139 or 445.
Risk factor :
None
Plugin output :
The remote Operating System is : Windows 5.1
The remote native lan manager is : Windows 2000 LAN Manager
The remote SMB Domain Name is : BEST
Nessus ID : 10785
Information found on port microsoft-ds (445/tcp)
Information found on port microsoft-ds (445/tcp)
Synopsis :
Access the remote Windows Registry.
Description :
It was not possible to connect to PIPE\winreg on the remote host.
If you intend to use Nessus to perform registry-based checks, the
registry checks will not work because the 'Remote Registry Access'
service (winreg) has been disabled on the remote host or can not be
connected to with the supplied credentials.
Risk factor :
None
Nessus ID : 10400
Information found on port microsoft-ds (445/tcp)
Synopsis :
It is possible to obtain remote host SID.
Description :
By emulating the call to LsaQueryInformationPolicy() it was
possible to obtain the host SID (Security Identifier).
The host SID can then be used to get the list of local users.
Risk factor :
None
Plugin output :
The remote host SID value is :
1-5-21-1907781795--213974095-110241057
CVE : CVE-2000-1200
BID : 959
Nessus ID : 10859
Information found on port microsoft-ds (445/tcp)
Synopsis :
It is possible to enumerate local users.
Description :
Using the host SID, it is possible to enumerates the local
users on the remote Windows system. (we only enumerated users
name whose ID is between 1000 and 2000 or whatever preferences
you set).
Risk factor :
None
Plugin output :
- Administrator account name : Administrator (id 500)
- Guest account name : Guest (id 501)
- HelpServicesGroup (id 1001)
- SUPPORT_388945a0 (id 1002)
- HelpAssistant (id 1004)
- ADMIN (id 1005)
- __vmware__ (id 1006)
- __vmware_user__ (id 1007)
- LNSS_MONITOR_USR (id 1008)
- dave (id 1011)
- ASPNET (id 1012)
- DONQ (id 1013)
CVE : CVE-2000-1200
BID : 959
Nessus ID : 10860
Information found on port general/tcp
Information found on port general/tcp
Information found on port general/tcp
Information about this scan :
Nessus version : 3.0.0
Plugin feed version : 200512092304
Type of plugin feed : Release
Scanner IP : 200.100.100.234
Port scanner(s) : nessus_tcp_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : no
Max hosts : 20
Max checks : 4
Scan Start Date : 2005/12/29 7:53
Scan duration : 410 sec
Nessus ID : 19506
Information found on port general/icmp
Synopsis :
It is possible to determine the exact time set on the remote host.
Description :
The remote host answers to an ICMP timestamp request. This allows an attacker
to know the date which is set on your machine.
This may help him to defeat all your time based authentication protocols.
Solution : filter out the ICMP timestamp requests (13), and the outgoing ICMP
timestamp replies (14).
Risk factor :
None / CVSS Base Score : 0
(AV:R/AC:L/Au:NR/C:N/A:N/I:N/B:N)
CVE : CVE-1999-0524
Nessus ID : 10114
Information found on port general/icmp
Here is the route recorded between 200.100.100.234 and 200.100.100.227 :
200.100.100.227.
Nessus ID : 12264
Information found on port general/udp
For your information, here is the traceroute from 200.100.100.234 to
200.100.100.227 :
200.100.100.234
200.100.100.227
Nessus ID : 10287
Information found on port netbios-ns (137/tcp)
Synopsis :
It is possible to obtain the network name of the remote host.
Description :
The remote host listens on udp port 137 and replies to NetBIOS
nbtscan requests.
By sending a wildcard request it is possible to obtain the name of
the remote system and the name of its domain.
Risk factor :
None
Plugin output :
The following 4 NetBIOS names have been gathered :
BEST = Computer name
WORKGROUP = Workgroup / Domain name
BEST = File Server Service
WORKGROUP = Browser Service Elections
The remote host has the following MAC address on its adapter :
00:c0:9f:6e:37:44
CVE : CVE-1999-0621
Nessus ID : 10150
This file was generated by Nessus, the
open-sourced security scanner.
| 










