|
Fedora Core 1 Nessus
Scan
The following is sample output
from a Nessus Scan with all plugins enabled against a default build of Fedora
Core 1 with no patches applied. A number of extra ports have also been
opened to show the results obtained. Obviously this machine is very
insecure and open to a great number of possible exploits due to the lack of
patching. You can also tell by the Security notes that a great number of
superfluous services are also running which need not be:
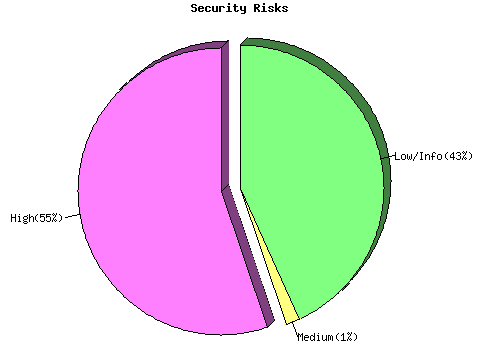
FC1Repartition of the level of the security problems :
List of open ports :
Warning found on port ssh (22/tcp)
The remote SSH daemon supports connections made
using the version 1.33 and/or 1.5 of the SSH protocol.
These protocols are not completely cryptographically
safe so they should not be used.
Solution :
If you use OpenSSH, set the option 'Protocol' to '2'
If you use SSH.com's set the option 'Ssh1Compatibility' to 'no'
Risk factor : Low
Nessus ID : 10882
Information found on port ssh (22/tcp)
Information found on port ssh (22/tcp)
Remote SSH version : SSH-1.99-OpenSSH_3.6.1p2
Remote SSH supported authentication : publickey,password,keyboard-interactive
Nessus ID : 10267
Information found on port ssh (22/tcp)
The remote SSH daemon supports the following versions of the
SSH protocol :
. 1.33
. 1.5
. 1.99
. 2.0
Nessus ID : 10881
Information found on port ssh (22/tcp)
The remote host seem to be running an SSH server which can allow
an attacker to determine the existence of a given login by comparing
the time the remote sshd daemon takes to refuse a bad password for a
non-existent login compared to the time it takes to refuse a bad password
for a valid login.
An attacker may use this flaw to set up a brute force attack against
the remote host.
Solution : Disable PAM support if you do not use it, upgrade to the newest
version of OpenSSH
Risk factor : Low
CVE : CVE-2003-0190
BID : 7342,
7467,
7482,
11781
Nessus ID : 11574
Information found on port sunrpc (111/tcp)
The RPC portmapper is running on this port.
An attacker may use it to enumerate your list
of RPC services. We recommend you filter traffic
going to this port.
Risk factor : Low
CVE : CVE-1999-0632,
CVE-1999-0189
BID : 205
Nessus ID : 10223
Information found on port sunrpc (111/tcp)
RPC program #100000 version 2 'portmapper' (portmap sunrpc rpcbind) is
running on this port
Nessus ID : 11111
Information found on port netbios-ssn (139/tcp)
Information found on port microsoft-ds (445/tcp)
Information found on port microsoft-ds (445/tcp)
Synopsis :
It is possible to obtain information about the remote os.
Description :
It is possible to get the remote operating system name and
version (Windows and/or Samba) by sending an authentication
request to port 139 or 445.
Risk factor :
None
Plugin output :
The remote Operating System is : Unix
The remote native lan manager is : Samba 3.0.0-15
The remote SMB Domain Name is : FC1
Nessus ID : 10785
Information found on port microsoft-ds (445/tcp)
Information found on port microsoft-ds (445/tcp)
Sysnopsis :
It is possible to obtain network information.
Description :
It was possible to obtain the browse list of the remote
Windows system by send a request to the LANMAN pipe.
The browse list is the list of the nearest Windows systems
of the remote host.
Risk factor :
None
Plugin output :
Here is the browse list of the remote host :
BEST ( os: 0.0 )
FC1 ( os: 0.0 )
Nessus ID : 10397
Information found on port nessus (1241/tcp)
Information found on port nessus (1241/tcp)
Here is the TLSv1 server certificate:
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1 (0x1)
Signature Algorithm: md5WithRSAEncryption
Issuer: C=FR, ST=none, L=Paris, O=Nessus Users United, OU=Certification
Authority for FC1, CN=FC1/emailAddress=ca@FC1
Validity
Not Before: Sep 6 17:33:38 2005 GMT
Not After : Sep 6 17:33:38 2006 GMT
Subject: C=FR, ST=none, L=Paris, O=Nessus Users United, OU=Server certificate
for FC1, CN=FC1/emailAddress=nessusd@FC1
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Exponent: 65537 (0x10001)
X509v3 extensions:
Netscape Cert Type:
SSL Server
X509v3 Key Usage:
Digital Signature, Non Repudiation, Key Encipherment
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
9D:7E:D9:CB:CK:5E:2F:8F:0D:C5:07:3C:AAE:2E:C9:F7:67:AB:B4:70
X509v3 Authority Key Identifier:
keyid:CC:B6:FF:91:BB:5D:D1:D0:97:33:03:6E:BA:A2:D7:E7:D9:5B:76:65
DirName:/C=FR/ST=none/L=Paris/O=Nessus Users United/OU=Certification Authority
for FC1/CN=FC1/emailAddress=ca@FC1
serial:00
X509v3 Subject Alternative Name:
email:nessusd@FC1
X509v3 Issuer Alternative Name:
<EMPTY>
Signature Algorithm: md5WithRSAEncryption
67:3f:3k:81:g6:53:20:d2:82:2e:3k:59:25:b4:6f:41:33:3b:
13:f1:1b:8d:90:cd:aa:b0:a3:d2:fa:5a:b4:k8:2f:5c:f1:7d:
3f:64:f6:k9:de:74:20:e0:a6:4c:96:a6:05:39:42:34:9f:90:
65:0d
This TLSv1 server does not accept SSLv2 connections.
This TLSv1 server does not accept SSLv3 connections.
Nessus ID : 10863
Information found on port nessus (1241/tcp)
Synopsis :
A Nessus daemon is listening on the remote port.
Description :
A Nessus daemon is listening on the remote port. It is not
recommended to let anyone connect to this port.
Also, make sure that the remote Nessus installation has
been authorized.
Solution :
Filter incoming traffic to this port.
Risk factor :
None
Nessus ID : 10147
Information found on port shilp (2049/tcp)
Information found on port shilp (2049/tcp)
RPC program #100003 version 2 'nfs' (nfsprog) is running on this port
RPC program #100003 version 3 'nfs' (nfsprog) is running on this port
Nessus ID : 11111
Information found on port filenet-nch (32770/tcp)
Vulnerability found on port
general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-288
(gtk2).
GTK+ is a multi-platform toolkit for creating graphical user
interfaces. Offering a complete set of widgets, GTK+ is suitable for
projects ranging from small one-off tools to complete application
suites.
Update Information:
During testing of a previously fixed flaw in Qt (CVE-2004-0691), a flaw
was discovered in the BMP image processor of gtk2. An attacker could create
a carefully crafted BMP file which would cause an application to enter an
infinite loop and not respond to user input when the file was opened by
a victim. The Common Vulnerabilities and Exposures project (cve.mitre.org)
has assigned the name CVE-2004-0753 to this issue.
During a security audit Chris Evans discovered a stack and a heap
overflow in the XPM image decoder. An attacker could create a carefully
crafted
XPM file which could cause an application linked with gtk2 to crash or
possibly execute arbitrary code when the file was opened by a victim.
(CVE-2004-0782, CVE-2004-0783)
Chris Evans also discovered an integer overflow in the ICO image
decoder. An attacker could create a carefully crafted ICO file which could
cause
an application linked with gtk2 to crash when the file was opened by a
victim. (CVE-2004-0788)
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-288.shtml
Risk factor : High
CVE : CVE-2004-0691,
CVE-2004-0753,
CVE-2004-0783,
CVE-2004-0788
Nessus ID : 14743
Vulnerability found on port general/tcp
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-278 (gaim).
Gaim allows you to talk to anyone using a variety of messaging
protocols, including AIM (Oscar and TOC), ICQ, IRC, Yahoo!,
MSN Messenger, Jabber, Gadu-Gadu, Napster, and Zephyr. These
protocols are implemented using a modular, easy to use design.
To use a protocol, just add an account using the account editor.
Gaim supports many common features of other clients, as well as many
unique features, such as perl scripting and C plugins.
Gaim is NOT affiliated with or endorsed by America Online, Inc.,
Microsoft Corporation, or Yahoo! Inc. or other messaging service
providers.
Update Information:
0.82 update contains many bug and security improvements.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-278.shtml
Risk factor : High
CVE : CVE-2004-0785
BID : 11056
Nessus ID : 14373
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-169 (cvs).
CVS (Concurrent Version System) is a version control system that can
record the history of your files (usually, but not always, source
code). CVS only stores the differences between versions, instead of
every version of every file you have ever created. CVS also keeps a log
of who, when, and why changes occurred.
CVS is very helpful for managing releases and controlling the
concurrent editing of source files among multiple authors. Instead of
providing version control for a collection of files in a single
directory, CVS provides version control for a hierarchical collection
of directories consisting of revision controlled files. These
directories and files can then be combined together to form a software
release.
Update Information:
While investigating a previously fixed vulnerability, Derek Price
discovered a flaw relating to malformed 'Entry' lines which lead to a
missing NULL terminator. The Common Vulnerabilities and Exposures
project (cve.mitre.org) has assigned the name CVE-2004-0414 to this
issue.
Stefan Esser and Sebastian Krahmer conducted an audit of CVS and
fixed a number of issues that may have had security consequences.
Among the issues deemed likely to be exploitable were:
-- a double-free relating to the error_prog_name string
(CVE-2004-0416) -- an argument integer overflow (CVE-2004-0417) --
out-of-bounds writes in serv_notify (CVE-2004-0418).
An attacker who has access to a CVS server may be able to execute
arbitrary code under the UID on which the CVS server is executing.
Users of CVS are advised to upgrade to this updated package, which
updates the cvs package to version 1.11.17, which corrects these
issues.
Red Hat would like to thank Stefan Esser, Sebastian Krahmer, and
Derek Price for auditing, disclosing, and providing patches for these
issues.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-169.shtml
Risk factor : High
CVE : CVE-2004-0414,
CVE-2004-0417,
CVE-2004-0418
Nessus ID : 13723
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-268 (rsync).
Rsync uses a reliable algorithm to bring remote and host files into
sync very quickly. Rsync is fast because it just sends the differences
in the files over the network instead of sending the complete
files. Rsync is often used as a very powerful mirroring process or
just as a more capable replacement for the rcp command. A technical
report which describes the rsync algorithm is included in this
package.
Update Information:
This update backports a security fix to a path-sanitizing flaw that
affects rsync when it is used in daemon mode without also using
chroot.
For more information see
http://samba.org/rsync/
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-268.shtml
Risk factor : High
CVE : CVE-2004-0792
Nessus ID : 14320
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-286 (gdk-pixbuf).
The gdk-pixbuf package contains an image loading library used with the
GNOME GUI desktop environment. The GdkPixBuf library provides image
loading facilities, the rendering of a GdkPixBuf into various formats
(drawables or GdkRGB buffers), and a cache interface.
Update Information:
During testing of a previously fixed flaw in Qt (CVE-2004-0691), a flaw
was discovered in the BMP image processor of gdk-pixbuf. An attacker could
create a carefully crafted BMP file which would cause an application
to enter an infinite loop and not respond to user input when the file
was opened by a victim. The Common Vulnerabilities and Exposures project
(cve.mitre.org) has assigned the name CVE-2004-0753 to this issue.
During a security audit, Chris Evans discovered a stack and a heap
overflow in the XPM image decoder. An attacker could create a carefully
crafted
XPM file which could cause an application linked with gtk2 to crash or
possibly execute arbitrary code when the file was opened by a victim.
(CVE-2004-0782, CVE-2004-0783)
Chris Evans also discovered an integer overflow in the ICO image
decoder. An attacker could create a carefully crafted ICO file which could
cause
an application linked with gtk2 to crash when the file is opened by a
victim. (CVE-2004-0788)
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-286.shtml
Risk factor : High
CVE : CVE-2004-0691,
CVE-2004-0753,
CVE-2004-0783,
CVE-2004-0788
BID : 11195
Nessus ID : 14741
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-079
(kernel).
The kernel package contains the Linux kernel (vmlinuz), the core of your
Fedora Core Linux operating system. The kernel handles the basic functions
of the operating system: memory allocation, process allocation, device
input and output, etc.
Update Information:
Paul Starzetz discovered a flaw in return value checking in mremap() in the
Linux kernel versions 2.4.24 and previous that may allow a local attacker
to gain root privileges. No exploit is currently available; however this
issue is exploitable. The Common Vulnerabilities and Exposures project
(cve.mitre.org) has assigned the name CVE-2004-0077 to this issue.
Arjan van de Ven discovered a flaw in ncp_lookup() in ncpfs that could
allow local privilege escalation. ncpfs is only used to allow a system to
mount volumes of NetWare servers or print to NetWare printers. The Common
Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name
CVE-2004-0010 to this issue.
All users are advised to upgrade to these errata packages, which contain
backported security patches that correct these issues.
Red Hat would like to thank Paul Starzetz from ISEC for reporting the issue
CVE-2004-0077.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-079.shtml
Risk factor : High
CVE : CVE-2004-0010,
CVE-2004-0077
BID : 9686,
9691
Nessus ID : 13679
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-087
(libxml2).
This library allows to manipulate XML files. It includes support
to read, modify and write XML and HTML files. There is DTDs support
this includes parsing and validation even with complex DtDs, either
at parse time or later once the document has been modified. The output
can be a simple SAX stream or and in-memory DOM like representations.
In this case one can use the built-in XPath and XPointer implementation
to select subnodes or ranges. A flexible Input/Output mechanism is
available, with existing HTTP and FTP modules and combined to an
URI library.
Update Information:
Updated libxml2 packages are available to fix an overflow when parsing
the URI for remote resources.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-087.shtml
Risk factor : High
Nessus ID : 13681
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-294 (lha).
LHA is an archiving and compression utility for LHarc format archives.
LHA is mostly used in the DOS world, but can be used under Linux to
extract DOS files from LHA archives.
Install the lha package if you need to extract DOS files from LHA archives.
Update Information:
Lukasz Wojtow discovered a stack-based buffer overflow in all versions
of lha up to and including version 1.14. A carefully created archive could
allow an attacker to execute arbitrary code when a victim extracts or tests
the archive. The Common Vulnerabilities and Exposures project
(cve.mitre.org) has assigned the name CVE-2004-0769 to this issue.
Buffer overflows were discovered in the command line processing of all
versions of lha up to and including version 1.14. If a malicious user can
trick a victim into passing a specially crafted command line to the lha
command, it is possible that arbitrary code could be executed. The Common
Vulnerabilities and Exposures project (cve.mitre.org) has assigned the
names CVE-2004-0771 and CVE-2004-0694 to these issues.
Thomas Biege discovered a shell meta character command execution
vulnerability in all versions of lha up to and including 1.14. An attacker
could create a directory with shell meta characters in its name which could
lead to arbitrary command execution. The Common Vulnerabilities and
Exposures project (cve.mitre.org) has assigned the name CVE-2004-0745 to
this issue.
Users of lha should update to this updated package
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-294.shtml
Risk factor : High
CVE : CVE-2004-0694,
CVE-2004-0745,
CVE-2004-0769
Nessus ID : 14692
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-069
(XFree86).
XFree86 is an open source implementation of the X Window System. It
provides the basic low level functionality which full fledged
graphical user interfaces (GUIs) such as GNOME and KDE are designed
upon.
Update Information:
Updated XFree86 packages that fix a privilege escalation vulnerability are
now available.
XFree86 is an implementation of the X Window System, providing the core
graphical user interface and video drivers.
iDefense discovered two buffer overflows in the parsing of the 'font.alias'
file. A local attacker could exploit this vulnerability by creating a
carefully-crafted file and gaining root privileges.
The Common Vulnerabilities and Exposures project (cve.mitre.org) has
assigned the names CVE-2004-0083 and CVE-2004-0084 to these issues.
Additionally David Dawes discovered additional flaws in reading font files.
The Common Vulnerabilities and Exposures project (cve.mitre.org) has
assigned the name CVE-2004-0106 to these issues.
All users of XFree86 are advised to upgrade to these erratum packages,
which contain a backported fix and are not vulnerable to these issues.
Red Hat would like to thank David Dawes from XFree86 for the patches and
notification of these issues.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-069.shtml
Risk factor : High
CVE : CVE-2004-0083,
CVE-2004-0084,
CVE-2004-0106
Nessus ID : 13677
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-276
(krb5).
Kerberos V5 is a trusted-third-party network authentication system,
which can improve your network's security by eliminating the insecure
practice of cleartext passwords.
Update Information:
Kerberos is a networked authentication system which uses a trusted
third party (a KDC) to authenticate clients and servers to each
other.
Several double-free bugs were found in the Kerberos 5 KDC and
libraries. A remote attacker could potentially exploit these flaws to
execute arbitrary code. The Common Vulnerabilities and Exposures
project (cve.mitre.org) has assigned the names CVE-2004-0642 and
CVE-2004-0643 to these issues.
A double-free bug was also found in the krb524 server
(CVE-2004-0772), however this issue does not affect Fedora Core.
An infinite loop bug was found in the Kerberos 5 ASN.1 decoder
library. A remote attacker may be able to trigger this flaw and cause
a denial of service. The Common Vulnerabilities and Exposures project
(cve.mitre.org) has assigned the name CVE-2004-0644 to this issue.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-276.shtml
Risk Factor : High
CVE : CVE-2004-0642,
CVE-2004-0643,
CVE-2004-0644,
CVE-2004-0772
BID : 11078,
11079
Nessus ID : 14592
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-068 (netpbm).
The netpbm package contains a library of functions which support
programs for handling various graphics file formats, including .pbm
(portable bitmaps), .pgm (portable graymaps), .pnm (portable anymaps),
.ppm (portable pixmaps) and others.
Update Information:
This update of the netpbm package fixes some security holes found by the
Debian group.
An update to the latest version these packages provide is recommended to
every user of the netpbm programs and toosl.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-068.shtml
Risk factor : High
Nessus ID : 13676
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-284
(samba).
Samba is the protocol by which a lot of PC-related machines share
files, printers, and other information (such as lists of available
files and printers). The Windows NT, OS/2, and Linux operating systems
support this natively, and add-on packages can enable the same thing
for DOS, Windows, VMS, UNIX of all kinds, MVS, and more. This package
provides an SMB server that can be used to provide network services to
SMB (sometimes called 'Lan Manager') clients. Samba uses NetBIOS over
TCP/IP (NetBT) protocols and does NOT need the NetBEUI (Microsoft Raw
NetBIOS frame) protocol.
* Wed Aug 25 2004 Jay Fenlason <fenlason@redhat.com> 3.0.6-1.FC2
- Upgade to 3.0.6
include the following patches:
samba-3.0.5rc1-passwd.patch from me. This changes the character
used in the password field of the entries generated by winbind
from a 'x' to a '*'. 'x' means something special ('password is
in /etc/shadow') to another pam module.
samba-3.0.5pre1-smbclient-kerberos.patch from
Alexander Larsson (alexl@redhat.com). Make kerberized smbclient
work better.
samba-3.0.5pre1-use_authtok.patch from Nalin Dahyabhai
<nalin@redhat.com> Fix an apparent braino in pam_winbind.c and
correct Cristian Gafton's name
samba-3.0.6-schema.patch from Gerald (Jerry) Carter <jerry@samba.org>
Correct the LDAP schema
samba-3.0.5rc1-64bit-timestamps.patch from Ravikumar
(rkumar@hp.com) to allow correct timestamp handling on 64-bit
platforms and fix #126109.
samba-3.0.4-install.mount.smbfs.patch from Juanjo Villaplana
(villapla@si.uji.es) to prevent building the srpm from trashing
the installed /usr/bin/smbmount
* Thu May 20 2004 Jay Fenlason <fenlason@redhat.com> 3.0.4-2.FC1
- include -winbind patch from Gerald (Jerry) Carter (jerry@samba.org)
https://bugzilla.samba.org/show_bug.cgi?id=1315
to make winbindd work against Windows versions that do not have
128 bit encryption enabled.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-284.shtml
Risk Factor : High
CVE : CVE-2004-0686
Nessus ID : 14642
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-149
(krb5).
Kerberos V5 is a trusted-third-party network authentication system,
which can improve your network's security by eliminating the insecure
practice of cleartext passwords.
Update Information:
Bugs have been fixed in the krb5_aname_to_localname library function.
Specifically, buffer overflows were possible for all Kerberos
versions up to and including 1.3.3. The krb5_aname_to_localname
function translates a Kerberos principal name to a local account
name, typically a UNIX username. This function is frequently used
when performing authorization checks.
If configured with mappings from particular Kerberos principals to
particular UNIX user names, certain functions called by
krb5_aname_to_localname will not properly check the lengths of
buffers used to store portions of the principal name. If configured
to map principals to user names using rules, krb5_aname_to_localname
would consistently write one byte past the end of a buffer allocated
from the heap. The Common Vulnerabilities and Exposures project
(cve.mitre.org) has assigned the name CVE-2004-0523 to this issue.
Only configurations which enable the explicit mapping or rules-based
mapping functionality of krb5_aname_to_localname() are vulnerable.
These configurations are not the default.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-149.shtml
Risk factor : High
CVE : CVE-2004-0523
BID : 10448
Nessus ID : 13710
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-095 (openssl).
The OpenSSL toolkit provides support for secure communications between
machines. OpenSSL includes a certificate management tool and shared
libraries which provide various cryptographic algorithms and
protocols.
Update Information:
This update includes OpenSSL packages to fix two security issues
affecting OpenSSL 0.9.7a which allow denial of service attacks; CVE
CVE-2004-0079 and CVE CVE-2003-0851.
Also included are updates for the OpenSSL 0.9.6 and 0.9.6b
compatibility libraries included in Fedora Core 1, fixing a separate
issue which could also lead to a denial of service attack; CVE
CVE-2004-0081.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-095.shtml
Risk factor : High
CVE : CVE-2003-0851,
CVE-2004-0081
BID : 8970
Nessus ID : 13684
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-174
(libpng10).
The libpng10 package contains an old version of libpng, a library of
functions for creating and manipulating PNG (Portable Network Graphics)
image format files.
This package is needed if you want to run binaries that were linked
dynamically
with libpng 1.0.x.
Update Information:
During an audit of Red Hat Linux updates, the Fedora Legacy team found a
security issue in libpng that had not been fixed in Fedora Core. An
attacker could carefully craft a PNG file in such a way that
it would cause an application linked to libpng to crash or potentially
execute arbitrary code when opened by a victim.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-174.shtml
Risk factor : High
Nessus ID : 13728
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-219
(ethereal).
Ethereal is a network traffic analyzer for Unix-ish operating systems.
This package lays base for libpcap, a packet capture and filtering
library, contains command-line utilities, contains plugins and
documentation for ethereal. A graphical user interface is packaged
separately to GTK+ package.
Update Information:
Issues have been discovered in the following protocol dissectors:
* The iSNS dissector could make Ethereal abort in some cases.
(0.10.3 - 0.10.4) CVE-2004-0633
* SMB SID snooping could crash if there was no policy name for a
handle. (0.9.15 - 0.10.4) CVE-2004-0634
* The SNMP dissector could crash due to a malformed or missing
community string. (0.8.15 - 0.10.4) CVE-2004-0635
Impact:
It may be possible to make Ethereal crash or run arbitrary code by
injecting a purposefully malformed packet onto the wire or by convincing
someone to read a malformed packet trace file.
Resolution:
Upgrade to 0.10.5.
If you are running a version prior to 0.10.5 and you cannot upgrade, you
can disable all of the protocol dissectors listed above by selecting
Analyze->Enabled Protocols... and deselecting them from the list. For
SMB, you can alternatively disable SID snooping in the SMB protocol
preferences. However, it is strongly recommended that you upgrade to
0.10.5.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-219.shtml
Risk factor : High
CVE : CVE-2004-0633,
CVE-2004-0634,
CVE-2004-0635
Nessus ID : 13738
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-237 (libpng).
The libpng package contains a library of functions for creating and
manipulating PNG (Portable Network Graphics) image format files. PNG
is a bit-mapped graphics format similar to the GIF format. PNG was
created to replace the GIF format, since GIF uses a patented data
compression algorithm.
Libpng should be installed if you need to manipulate PNG format image
files.
several buffer overflows were found in libpng. An attacker could create
a carefully crafted PNG file in such a way that it would cause an
application linked with libpng to execute arbitrary code when the file
was opened by a victim.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-237.shtml
Risk factor : High
CVE : CVE-2002-1363,
CVE-2004-0597,
CVE-2004-0598,
CVE-2004-0599
BID : 10857
Nessus ID : 14208
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-119 (lha).
LHA is an archiving and compression utility for LHarc format archives.
LHA is mostly used in the DOS world, but can be used under Linux to
extract DOS files from LHA archives.
Install the lha package if you need to extract DOS files from LHA archives.
Update Information:
Ulf H rnhammar discovered two stack buffer overflows and two directory
traversal flaws in LHA. An attacker could exploit the buffer
overflows by creating a carefully crafted LHA archive in such a way
that arbitrary code would be executed when the archive is tested or
extracted by a victim. CVE-2004-0234. An attacker could exploit the
directory traversal issues to create files as the victim outside of
the expected directory. CVE-2004-0235.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-119.shtml
Risk factor : High
CVE : CVE-2004-0234,
CVE-2004-0235
Nessus ID : 13697
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-236
(libpng10).
The libpng10 package contains an old version of libpng, a library of
functions for creating and manipulating PNG (Portable Network Graphics)
image format files.
This package is needed if you want to run binaries that were linked
dynamically with libpng 1.0.x. The libpng package contains a library
of functions for creating and manipulating PNG (Portable Network Graphics)
image format files.
several buffer overflows have been discovered in libpng. An attacker
could create a carefully crafted PNG file in such a way that it would
cause an application linked with libpng to execute arbitrary code when
the file was opened by a victim.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-236.shtml
Risk factor : High
CVE : CVE-2002-1363,
CVE-2004-0597,
CVE-2004-0598,
CVE-2004-0599
BID : 10857
Nessus ID : 14207
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-173 (libpng).
The libpng package contains a library of functions for creating and
manipulating PNG (Portable Network Graphics) image format files. PNG
is a bit-mapped graphics format similar to the GIF format. PNG was
created to replace the GIF format, since GIF uses a patented data
compression algorithm.
Libpng should be installed if you need to manipulate PNG format image
files.
Update Information:
During an audit of Red Hat Linux updates, the Fedora Legacy team found a
security issue in libpng that had not been fixed in Fedora Core. An
attacker could carefully craft a PNG file in such a way that
it would cause an application linked to libpng to crash or potentially
execute arbitrary code when opened by a victim.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-173.shtml
Risk factor : High
Nessus ID : 13727
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-092 (tcpdump).
Tcpdump is a command-line tool for monitoring network traffic.
Tcpdump can capture and display the packet headers on a particular
network interface or on all interfaces. Tcpdump can display all of
the packet headers, or just the ones that match particular criteria.
Install tcpdump if you need a program to monitor network traffic.
Update Information:
Updated tcpdump, libpcap, and arpwatch packages fix vulnerabilities in
ISAKMP and RADIUS parsing.
Tcpdump is a command-line tool for monitoring network traffic.
George Bakos discovered flaws in the ISAKMP decoding routines of tcpdump
versions prior to 3.8.1. The Common Vulnerabilities and Exposures
project (cve.mitre.org) has assigned the name CVE-2003-0989 to this issue.
Jonathan Heusser discovered an additional flaw in the ISAKMP decoding
routines for tcpdump 3.8.1 and earlier. The Common Vulnerabilities and
Exposures project (cve.mitre.org) has assigned the name CVE-2004-0057 to
this issue.
Jonathan Heusser discovered a flaw in the print_attr_string function in
the RADIUS decoding routines for tcpdump 3.8.1 and earlier. The Common
Vulnerabilities and Exposures project (cve.mitre.org) has assigned the
name CVE-2004-0055 to this issue.
Remote attackers could potentially exploit these issues by sending
carefully-crafted packets to a victim. If the victim uses tcpdump, these
pakets could result in a denial of service, or possibly execute
arbitrary code as the 'pcap' user.
Users of tcpdump are advised to upgrade to these erratum packages, which
contain backported security patches and are not vulnerable to these issues.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-092.shtml
Risk factor : High
CVE : CVE-2003-0989,
CVE-2004-0055,
CVE-2004-0057
BID : 9423
Nessus ID : 13683
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-235 (sox).
SoX (Sound eXchange) is a sound file format converter SoX can convert
between many different digitized sound formats and perform simple
sound manipulation functions, including sound effects.
Update Information:
Updated sox packages that fix buffer overflows in the WAV file handling
code are now available.
Buffer overflows existed in the parsing of WAV file header fields. It
was possible that a malicious WAV file could have caused arbitrary code to
be executed when the file was played or converted.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-235.shtml
Risk factor : High
CVE : CVE-2004-0557
BID : 10819
Nessus ID : 13850
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-270 (qt).
Qt is a GUI software toolkit which simplifies the task of writing and
maintaining GUI (Graphical User Interface) applications
for the X Window System.
Qt is written in C++ and is fully object-oriented.
This package contains the shared library needed to run qt
applications, as well as the README files for qt.
Update Information:
During a security audit, Chris Evans discovered a heap overflow in the BMP
image decoder in Qt versions prior to 3.3.3. An attacker could create a
carefully crafted BMP file in such a way that it would cause an application
linked with Qt to crash or possibly execute arbitrary code when the file
was opened by a victim. The Common Vulnerabilities and Exposures project
(cve.mitre.org) has assigned the name CVE-2004-0691 to this issue.
Additionally, various flaws were discovered in the GIF, XPM, and JPEG
decoders in Qt versions prior to 3.3.3. An attacker could create carefully
crafted image files in such a way that it could cause an application linked
against Qt to crash when the file was opened by a victim. The Common
Vulnerabilities and Exposures project (cve.mitre.org) has assigned the
names CVE-2004-0692 and CVE-2004-0693 to these issues.
Users of Qt should update to these updated packages which contain
backported patches and are not vulnerable to these issues.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-270.shtml
Risk factor : High
CVE : CVE-2004-0691,
CVE-2004-0693
Nessus ID : 14348
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-126 (cvs).
CVS (Concurrent Version System) is a version control system that can
record the history of your files (usually, but not always, source
code). CVS only stores the differences between versions, instead of
every version of every file you have ever created. CVS also keeps a log
of who, when, and why changes occurred.
CVS is very helpful for managing releases and controlling the
concurrent editing of source files among multiple authors. Instead of
providing version control for a collection of files in a single
directory, CVS provides version control for a hierarchical collection
of directories consisting of revision controlled files. These
directories and files can then be combined together to form a software
release.
Update Information:
Stefan Esser discovered a flaw in cvs where malformed 'Entry' lines
could cause a heap overflow. An attacker who has access to a CVS
server could use this flaw to execute arbitrary code under the UID
which the CVS server is executing. The Common Vulnerabilities and
Exposures project (cve.mitre.org) has assigned the name CVE-2004-0396
to this issue.
This update includes a patch by Derek Price, based on a patch by
Stefan Esser, which corrects this flaw.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-126.shtml
Risk factor : High
CVE : CVE-2004-0396
Nessus ID : 13701
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-063
(kernel).
The kernel package contains the Linux kernel (vmlinuz), the core of your
Fedora Core Linux operating system. The kernel handles the basic functions
of the operating system: memory allocation, process allocation, device
input and output, etc.
* Mon Jan 26 2004 Dave Jones <davej@redhat.com>
- Fix error in wan config files that broke some configurators.
- Reenable VIA DRI.
* Fri Jan 16 2004 Dave Jones <davej@redhat.com>
- Merge VM updates from post 2.4.22
- Fix AMD64 ptrace security hole. (CVE-2004-0001)
- Fix NPTL SMP hang.
- Merge bits from 2.4.25pre
- R128 DRI limits checking. (CVE-2004-0003)
- Various ymfpci fixes.
- tmpfs readdir does not update dir atime
- Minor IPV4/Netfilter changes.
- Fix userspace dereferencing bug in USB Vicam driver.
- Merge a few more bits from 2.4.23pre
- Numerous tmpfs fixes.
- Use list_add_tail in buffer_insert_list
- Correctly dequeue SIGSTOP signals in kupdated
- Update laptop-mode patch to match mainline.
* Wed Jan 14 2004 Dave Jones <davej@redhat.com>
- Merge a few more missing netfilter fixes from upstream.
* Tue Jan 13 2004 Dave Jones <davej@redhat.com>
- Reenable Tux.
- Lots of updates from the 2.4.23 era.
* Mon Jan 12 2004 Dave Jones <davej@redhat.com>
- Avoid deadlocks in USB storage.
* Fri Jan 09 2004 Dave Jones <davej@redhat.com>
- Fix thread creation race.
* Thu Jan 08 2004 Dave Jones <davej@redhat.com>
- USB storage: Make Pentax Optio S4 work
- Config file tweaking. Only enable CONFIG_SIBLINGS_2
on the kernels that need it.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-063.shtml
Risk factor : High
CVE : CVE-2004-0001,
CVE-2004-0003
BID : 9429,
9570
Nessus ID : 13675
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-152
(ethereal).
Ethereal is a network traffic analyzer for Unix-ish operating systems.
This package lays base for libpcap, a packet capture and filtering
library, contains command-line utilities, contains plugins and
documentation for ethereal. A graphical user interface is packaged
separately to GTK+ package.
Update Information:
Issues have been discovered in the following protocol dissectors:
* A SIP packet could make Ethereal crash under specific conditions,
as described in the following message:
http://www.ethereal.com/lists/ethereal-users/200405/msg00018.html
(0.10.3).
* The AIM dissector could throw an assertion, causing Ethereal to
terminate abnormally (0.10.3).
* It was possible for the SPNEGO dissector to dereference a null
pointer, causing a crash (0.9.8 to 0.10.3).
* The MMSE dissector was susceptible to a buffer overflow. (0.10.1
to 0.10.3).
All users of Ethereal are strongly encouraged to update to these latest
packages.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-152.shtml
Risk factor : High
Nessus ID : 13712
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-116 (rsync).
Rsync uses a reliable algorithm to bring remote and host files into
sync very quickly. Rsync is fast because it just sends the differences
in the files over the network instead of sending the complete
files. Rsync is often used as a very powerful mirroring process or
just as a more capable replacement for the rcp command. A technical
report which describes the rsync algorithm is included in this
package.
Update Information:
Rsync before 2.6.1 does not properly sanitize paths when running a
read/write daemon without using chroot. This could allow a remote attacker
to write files outside of the module's 'path', depending on the privileges
assigned to the rsync daemon. Users not running an rsync daemon, running a
read-only daemon, or running a chrooted daemon are not affected by this
issue. The Common Vulnerabilities and Exposures project (cve.mitre.org)
has assigned the name CVE-2004-0426 to this issue.
Updated packages were made available in June 2004 however the original
update notification email did not make it to fedora-announce-list at
that time.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-116.shtml
Risk factor : High
CVE : CVE-2004-0426
Nessus ID : 13695
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-080
(kernel).
The kernel package contains the Linux kernel (vmlinuz), the core of your
Fedora Core Linux operating system. The kernel handles the basic functions
of the operating system: memory allocation, process allocation, device
input and output, etc.
Update Information:
The previous security errata (2.4.22-1.2173) unfortunatly contained a bug
which made some systems unbootable, due to breakage in the aacraid scsi
driver. This update contains no further changes vs 2173.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-080.shtml
Risk factor : High
Nessus ID : 13680
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-106
(libpng10).
The libpng10 package contains an old version of libpng, a library of
functions for creating and manipulating PNG (Portable Network Graphics)
image format files.
This package is needed if you want to run binaries that were linked
dynamically
with libpng 1.0.x.
* Mon Apr 19 2004 Matthias Clasen <mclasen redhat com>
- fix a possible out-of-bounds read in the error message
handler. #121229
* Tue Mar 02 2004 Elliot Lee <sopwith redhat com>
- rebuilt
* Fri Feb 13 2004 Elliot Lee <sopwith redhat com>
- rebuilt
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-106.shtml
Risk factor : High
Nessus ID : 13689
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-061
(mutt).
Mutt is a text-mode mail user agent. Mutt supports color, threading,
arbitrary key remapping, and a lot of customization.
You should install mutt if you have used it in the past and you prefer
it, or if you are new to mail programs and have not decided which one
you are going to use.
Update Information:
This package fixes CVE-2004-0078, where a specifc message could cause
mutt to crash. This is the vulnerability fixed in the recently released
mutt-1.4.2.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-061.shtml
Risk factor : High
CVE : CVE-2004-0078
BID : 9641
Nessus ID : 13674
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-115 (iproute).
The iproute package contains networking utilities (ip and rtmon, for
example) which are designed to use the advanced networking
capabilities of the Linux 2.4.x and 2.6.x kernel.
Update Information:
This update of the iproute package fixes a security problem found in netlink.
See CVE-2003-0856. All users of the netlink application are very strongly
advised to update to these latest packages.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-115.shtml
Risk factor : High
CVE : CVE-2003-0856
BID : 9092
Nessus ID : 13694
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-304
(samba).
Samba is the protocol by which a lot of PC-related machines share
files, printers, and other information (such as lists of available
files and printers). The Windows NT, OS/2, and Linux operating systems
support this natively, and add-on packages can enable the same thing
for DOS, Windows, VMS, UNIX of all kinds, MVS, and more. This package
provides an SMB server that can be used to provide network services to
SMB (sometimes called 'Lan Manager') clients. Samba uses NetBIOS over
TCP/IP (NetBT) protocols and does NOT need the NetBEUI (Microsoft Raw
NetBIOS frame) protocol.
Update Information:
This update addcesses two DoS errors in Samba-3.0.6
This update may also fix other problems some people experienced with
Samba-3.0.6.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-304.shtml
Risk factor : High
CVE : CVE-2004-0808
Nessus ID : 14716
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-105 (libpng).
The libpng package contains a library of functions for creating and
manipulating PNG (Portable Network Graphics) image format files. PNG
is a bit-mapped graphics format similar to the GIF format. PNG was
created to replace the GIF format, since GIF uses a patented data
compression algorithm.
Libpng should be installed if you need to manipulate PNG format image
files.
* Mon Apr 19 2004 Matthias Clasen <mclasen redhat com>
- fix a possible out-of-bounds read in the error message
handler. #121229
* Tue Mar 02 2004 Elliot Lee <sopwith redhat com>
- rebuilt
* Fri Feb 27 2004 Mark McLoughlin <markmc redhat com> 2:1.2.2-19
- rebuild with changed bits/setjmp.h on ppc
* Fri Feb 13 2004 Elliot Lee <sopwith redhat com>
- rebuilt
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-105.shtml
Risk factor : High
Nessus ID : 13688
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-120 (tcpdump).
Tcpdump is a command-line tool for monitoring network traffic.
Tcpdump can capture and display the packet headers on a particular
network interface or on all interfaces. Tcpdump can display all of
the packet headers, or just the ones that match particular criteria.
Install tcpdump if you need a program to monitor network traffic.
Update Information:
Tcpdump is a command-line tool for monitoring network traffic.
Tcpdump v3.8.1 and earlier versions contained multiple flaws in the
packet display functions for the ISAKMP protocol. Upon receiving
specially crafted ISAKMP packets, TCPDUMP would try to read beyond
the end of the packet capture buffer and subsequently crash.
Users of tcpdump are advised to upgrade to these erratum packages, which
contain backported security patches and are not vulnerable to these issues.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-120.shtml
Risk factor : High
CVE : CVE-2004-0183
Nessus ID : 13698
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-300 (imlib).
Imlib is a display depth independent image loading and rendering
library. Imlib is designed to simplify and speed up the process of
loading images and obtaining X Window System drawables. Imlib
provides many simple manipulation routines which can be used for
common operations.
Install imlib if you need an image loading and rendering library for
X11R6, or if you are installing GNOME. You may also want to install
the imlib-cfgeditor package, which will help you configure Imlib.
Update Information:
Several heap overflow vulnerabilities have been found in the imlib BMP
image handler. An attacker could create a carefully crafted BMP file in
such a way that it would cause an application linked with imlib to
execute
arbitrary code when the file was opened by a victim. The Common
Vulnerabilities and Exposures project (cve.mitre.org) has assigned the
name
CVE-2004-0817 to this issue.
Users of imlib should update to this updated package which contains
backported patches and is not vulnerable to these issues.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-300.shtml
Risk factor : High
CVE : CVE-2004-0817
Nessus ID : 14703
Vulnerability found on port general/tcp
The remote host is missing the patch for the advisory FEDORA-2004-110 (cvs).
CVS (Concurrent Version System) is a version control system that can
record the history of your files (usually, but not always, source
code). CVS only stores the differences between versions, instead of
every version of every file you have ever created. CVS also keeps a log
of who, when, and why changes occurred.
CVS is very helpful for managing releases and controlling the
concurrent editing of source files among multiple authors. Instead of
providing version control for a collection of files in a single
directory, CVS provides version control for a hierarchical collection
of directories consisting of revision controlled files. These
directories and files can then be combined together to form a software
release.
Update Information:
The client for CVS before 1.11.15 allows a remote malicious CVS server
to create arbitrary files using certain RCS diff files that use
absolute pathnames during checkouts or updates.
Updated packages were made available in April 2004 however the original
update notification email did not make it to fedora-announce-list at
that time.
Solution :
http://www.fedoranews.org/updates/FEDORA-2004-110.shtml
Risk factor : High
CVE : CVE-2004-0180
Nessus ID : 13691
Information found on port general/tcp
Information found on port general/tcp
The output of "uname -a" is :
Linux FC1 2.4.22-1.2149.nptlsmp #1 SMP Wed Jan 7 12:51:51 EST 2004 i686 i686
i386 GNU/Linux
The remote Fedora system is :
Fedora Core release 1 (Yarrow)
Local security checks have been enabled for this host.
Nessus ID : 12634
Information found on port general/tcp
Information about this scan :
Nessus version : 3.0.0
Plugin feed version : 200512092304
Type of plugin feed : Release
Scanner IP : 192.168.0.1
Port scanner(s) : nessus_tcp_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : no
Max hosts : 20
Max checks : 4
Scan Start Date : 2005/12/29 7:42
Scan duration : 414 sec
Nessus ID : 19506
Information found on port unknown (935/tcp)
RPC program #100011 version 1 'rquotad' (rquotaprog quota rquota) is
running on this port
RPC program #100011 version 2 'rquotad' (rquotaprog quota rquota) is running
on this port
Nessus ID : 11111
Information found on port unknown (954/tcp)
RPC program #100005 version 1 'mountd' (mount showmount) is running on this
port
RPC program #100005 version 2 'mountd' (mount showmount) is running on this
port
RPC program #100005 version 3 'mountd' (mount showmount) is running on this
port
Nessus ID : 11111
Information found on port unknown (50553/tcp)
RPC program #100021 version 1 'nlockmgr' is running on this port
RPC program #100021 version 3 'nlockmgr' is running on this port
RPC program #100021 version 4 'nlockmgr' is running on this port
Nessus ID : 11111
Information found on port sunrpc (111/udp)
RPC program #100000 version 2 'portmapper' (portmap sunrpc rpcbind) is
running on this port
Nessus ID : 11111
Information found on port unknown (932/udp)
RPC program #100011 version 1 'rquotad' (rquotaprog quota rquota) is
running on this port
RPC program #100011 version 2 'rquotad' (rquotaprog quota rquota) is running
on this port
Nessus ID : 11111
Information found on port unknown (951/udp)
RPC program #100005 version 1 'mountd' (mount showmount) is running on this
port
RPC program #100005 version 2 'mountd' (mount showmount) is running on this
port
RPC program #100005 version 3 'mountd' (mount showmount) is running on this
port
Nessus ID : 11111
Information found on port shilp (2049/udp)
RPC program #100003 version 2 'nfs' (nfsprog) is running on this port
RPC program #100003 version 3 'nfs' (nfsprog) is running on this port
Nessus ID : 11111
Information found on port unknown (32832/udp)
RPC program #100021 version 1 'nlockmgr' is running on this port
RPC program #100021 version 3 'nlockmgr' is running on this port
RPC program #100021 version 4 'nlockmgr' is running on this port
Nessus ID : 11111
Information found on port netbios-ns (137/tcp)
Synopsis :
It is possible to obtain the network name of the remote host.
Description :
The remote host listens on udp port 137 and replies to NetBIOS
nbtscan requests.
By sending a wildcard request it is possible to obtain the name of
the remote system and the name of its domain.
Risk factor :
None
Plugin output :
The following 7 NetBIOS names have been gathered :
FC1 = Computer name
FC1 = Messenger Service
FC1 = File Server Service
__MSBROWSE__ = Master Browser
WORKGROUP = Workgroup / Domain name
WORKGROUP = Master Browser
WORKGROUP = Browser Service Elections
This SMB server seems to be a SAMBA server (MAC address is NULL).
CVE : CVE-1999-0621
Nessus ID : 10150
| 










