|
 |
 |
 |
 |
  |
|||
 |
 |
 |
|
|
SAINT Professional
Saint Professional is a commercial off-the-shelf (COTS) suite combining two distinct tools rolled into one easy to use management interface, the SAINTscanner and SAINTexploit. These in combination make it an extensible fully integrated vulnerability assessment and penetration testing toolkit.
SAINTscanner can be used to:
Identify vulnerabilities on network devices, OS, desktop applications, Web applications, databases etc. Detect and fix possible weaknesses in a networks security before they can be exploited by intruders. Anticipate and prevent common system vulnerabilities. Demonstrate compliance with current government/ industry regulations (PCI DSS, FISMA, SOX, HIPAA etc.) Perform configuration audits with policies defined by FDCC & USGCB. Manage and schedule scans across large enterprises with the SAINTmanager remote management console. Perform content scanning for data that should not be stored on desktops/servers. Generate vulnerability assessment reports quickly and easily in multiple formats.
SAINTexploit can be used to:
Exploit vulnerabilities found by SAINTscanner. Carry out social engineering attacks such as phishing and flash drive autoplay. Automate penetration testing or run individual exploits against targets on demand. Emulate Web sites with built in design templates and e-mail forgery tools to facilitate client-side attacks. Tunnel through networks allowing penetration tests to be run from an exploited target.
SAINT Professional is available from here.
System Requirements:
Linux, Unix, or Mac OS X platform
Disk Space/memory 100 MB to run Additional space for optional packages (e.g., Samba, NMAP, OpenSSL, OpenSSH) 2 GB of RAM is recommended
Pre-requisites >= PERL 5.004 Web browser (IE, Firefox, Safari)
Installation:
Once logged in to the customer area, there is a choice to install from source or to utilise a pre-configured virtual machine which is available from here
This password is also required when you start the SAINT application from the terminal.
Once started SAINT will try and auto update and then auto open the default browser:
SAINTexpress Copyright 2001-2011 SAINT Corporation Retrieving updates for version 7.7.17... Checking updates... Updating config/policy/pwguess.conf Updating perl/misc.pl ---abridged--- Updating html/running/saint_run_form.pl Updated to version 7.8 Reconfiguring... ---abridged--- Retrieving updates for version 7.8...
The key is generated in the format:
saint.key SAINTscanner
SAINTscanner provides the ability to carry out both pre-defined and custom policy based vulnerability assessments. It is extensible and easy to setup, especially custom policies and options.
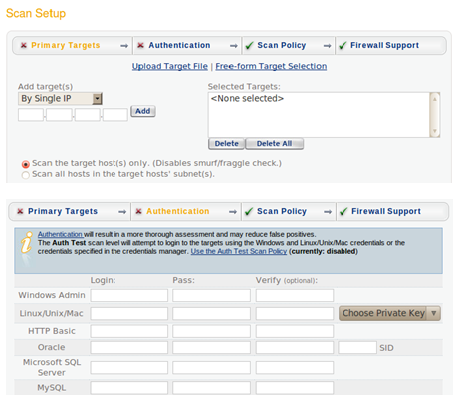
Selecting a Policy/ Creating a Custom Scan Policy
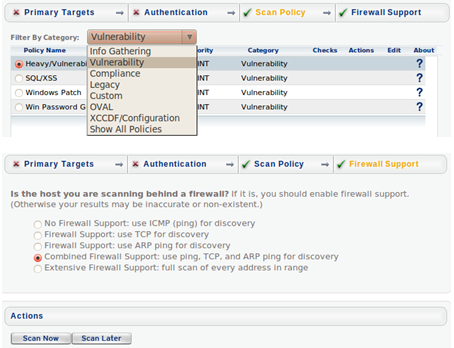
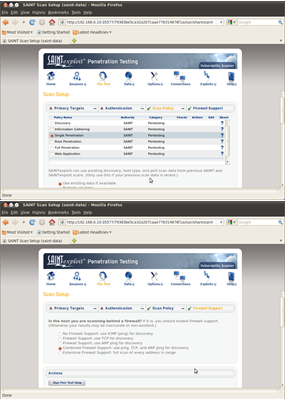
Selecting Scan Options allows the user to select a policy to use for the vulnerability scan, each policy then can be adapted to suit, in the example the probe options can be adapted to suit and then the actual policy in this case a Heavy Vulnerability Scan has been selected.
If this does not suit a user may at this point click on Set up custom scan and a list of vulnerability checks are displayed, all currently disabled. Each required section can be enabled as required or expanded and individual checks carried out.
Carrying Out a Scan
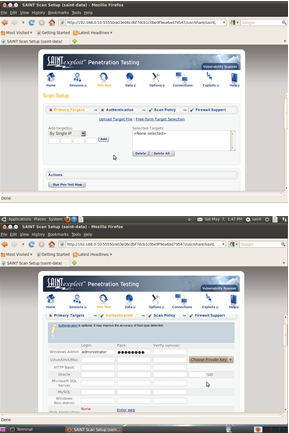
Step 1 Insert IP Range/ Address or Upload Target List Step 2 Type in credentials
Step 3 Select Scan Policy Type Step 4 Determine Firewall settings for Target Step 5 Select Scan Now
SAINTexploit
As previously mentioned, SAINTexploit can either automate a pen test, provide the tester with the ability to select single exploits to utilise or provide a client-side attack framework with which users once enticed to visit pre-defined and built websites are automatically exploited. Specially crafted emails can be auto-generated, a user on receipt of these mails may click the varied links and are directed to an already pre-configured exploit server.
Different levels of penetration tests can be carried out:
Conducting a test is fairly straight forward, once any prior configuration has been carried out, callback ports, timeouts etc. Just select Pen Test then go through the following 4 steps. Once complete select run pen test now.
Step 1 Insert IP Range/ Address or Upload Target List Step 3 Select Penetration Test Type Step 2 Type in credentials Step 4 Determine Firewall settings for Target
Post Exploitation
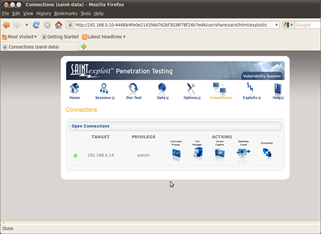
Once a host has been successfully exploited, navigating to the connections tab provides the ability to directly interact with the session. SAINTexploit provides four useful tools in this tab to allow interactive access to the session and a disconnect button to close any outstanding connection:
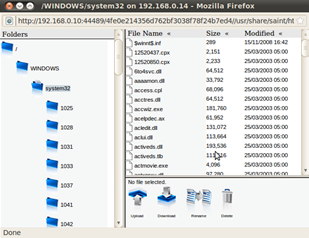
Figure 1 Admin Connection to Exploited 2K3 Server. Figure 2 File Manager on Exploited host. Gives the ability to perform numerous actions. Opened via the connections tab, ability to upload/ download/ rename files.
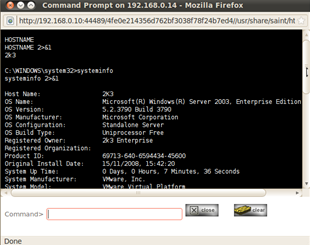
Figure 3 Command Prompt on Exploited host. Figure 4 Screenshot Tool against Exploited host. Opened via the connections tab, run DOS commands. Opened via the connections tab, grab screenshot for report etc.
Exploit Tools
E-mail attachment execution This tool sends an e-mail attachment which, when executed, establishes a command connection. This tool requires a user to execute the e-mail attachment in order to succeed.
Flash drive/CD autoplay command execution This tool allows you to create a USB flash drive which, when inserted into a Windows computer, prompts a user to run a program which creates a command connection.
Harvest e-mail addresses Uses publicly available information such as Internet search engines, network registrars and public key servers to harvest a list of e-mail addresses for automating client type exploits.
Harvest Metadata This tool searches the Internet for PDF and Microsoft Office files in the given domain, and extracts the metadata from those files. Keystroke Logger.
Password Hash Grabber This tool grabs the windows SAM file or password hashes of the target.
Perform DNS zone transfer.
Phishing tool This tool serves an HTML form which collects information from users. Read Outlook/ Outlook Express Address Books.
Retrieve website passwords stored by IE.
Reverse Shell Applet Delivers a signed java applet, embedded in an HTML page, to the user who is presented with a signed digital certificate which, when accepted, establishes a reverse shell connection back to the exploit server.
Upload command to startup folder Once uploaded a connection is established the next time the computer starts.
SAINTwriter is a component of SAINT that allows you to generate a variety of customised reports. SAINTwriter features eight pre-configured reports, eight report formats (HTML, Frameless HTML, Simple HTML, PDF, XML, text, tab-separated text, and comma-separated text), and over 100 configuration options for custom reports.
Note:- For Trend Analysis reports only: Choose two or more data sets you wish to be included in the trend analysis.
Copies of reports are available here and here
Overall Assessment
I have used several exploit frameworks during the course of my many roles, Core Impact, CANVAS, Metasploit etc. each of which has there own unique selling points, strengths, weaknesses and foibles. SAINT Professional ranks highly within these offerings. The combination of scanner and exploit framework is an excellent combination providing a one stop facility allowing the tester to carry out the full suite of their potential roles be they compliance, audit, vulnerability assessment or penetration test. In essence it is extensible, highly useful, easy to learn and very adaptable with the ability to define custom vulnerability assessment policies.
Strengths:
Weaknesses:
Note: - Reporting is both a strength and weakness, some of the information I felt was quite generic and not fully tailored to the scan/ test carried out however, the different levels of reporting via vulnerability, host, overview, summary etc and formats producible was excellent.
Future Versions
Version 8 of SAINT Professional should be out later this year and from early indications, a number of the points I have made (below) are already being reviewed and worked on together with some exciting enhancements. Although I really like this product now, especially its integration, I am really looking forward to evaluating and using it in the field.
Suggestions for future versions
After carrying out a fair amount of testing with the product, a few suggestions for improvement to the user experience were identified. These though are for the most part purely cosmetic in nature and do not detract from the excellent offering from the SAINT Corporation and are solely based on the authors personal preferences and use of the tool to perform multiple tests.
SAINTscanner has a few pre-defined policies and checks that can be enabled and customised i.e. have checks for windows machines, could this be extended to have pre-defined tests for other OS - RHEL, Solaris, Cisco that can be easily enabled.
A few of the configuration options for example the import of SCAP files allow for manual import and update, however, after the process is complete the open window is left there requiring the user to use the x to close it, no close widget is present, a more rounded solution would to have an auto close on successful completion of the task.
SAINTexploit single penetration test seems to try all available tests against the target dependant on the identified OS and open ports. Sometimes this may be nugatory effort and also increase the risk against the target trying an exploit against a service, albeit with the same open port that is not running. It would be beneficial to tune the test if prior knowledge is already known about the varied applications and services the target is running, in a similar way that you can tune SAINTscanner to perform bespoke scans based on custom policies.
SAINTexploit has 4 tools available to the tester from the connections tab, command, screenshot, file manager etc, it may be prudent to enhance and populate this section further with a number of the other tools; password grab et al which would be run once a connection has been gained. To run this and other tools a tester must navigate to the exploit tools section to execute.
The file explorer window with upload/ download and rename although functional could be enhanced with a norton commander/ explorer type window for drag and drop.
It did not seem possible to copy and paste anything from the SAINTwriter html reports to another browser window/ tab, yet the highlighted text was available directly to the terminal and also across vmware tool bridge to Windows 7 host.
Make available on the Windows platform.
Errors Encountered
During testing a couple of errors were observed in the terminal and within the web browser, these though seemed to be nothing of any major importance and the tool did not seem to display any negative side effects due to them.
SAINTscanner error, heavy scan against a Buffalo LinkStation Live 1TB MultiMedia Network Attached Storage, report generation, display and save:
GConf Error: Failed to contact configuration server; some possible causes are that you need to enable TCP/IP networking for ORBit, or you have stale NFS locks due to a system crash. See http://projects.gnome.org/gconf/ for information. (Details - 1: Failed to get connection to session: /bin/dbus-launch terminated abnormally without any error message)
** (evince:1982): WARNING **: Failed to connect to the session bus: /bin/dbus-launch terminated abnormally without any error message
SAINTexploit error, single penetration test against a Buffalo LinkStation Live 1TB MultiMedia Network Attached Storage:
sh: Syntax error: Unterminated quoted string sh: Syntax error: Unterminated quoted string
A new tab was created when the test started and an error message displayed in old tab.
'_' is unprintable in png image |
IT Security News:
Pen Testing Framework:
Information:
|
| © VulnerabilityAssessment.co.uk 11 May 2011 |
|